Prepare for the unexpected.
A critical IT service or a full data center outage is not just an operations problem; it is a business problem. The cost of unplanned outages can reverberate far and wide affecting revenue, reputation, and customer loyalty.
With the enterprise's increased dependency on IT and the increased interdependency of systems, cascading failures can cause significant impact, and outages of any type are unacceptable. In a world increasingly driven by digital business, unplanned outages can be fatal.
Vigilance and investment are the best stance when it comes to IT Service Continuity Management (ITSCM).

David-Kenneth Group’s ITSCM philosophy is based on years of working with various standard industry recovery and service continuity methodologies. We believe ITSCM is a custom fit that must support the continuity of an organization’s business operations in both an affordable and sustainable way. Our goal is to help you understand, optimize, and rightsize your IT landscape to respond to any kind of outage that would affect your organization.”
Senior Disaster Resiliency Architect
David-Kenneth Group

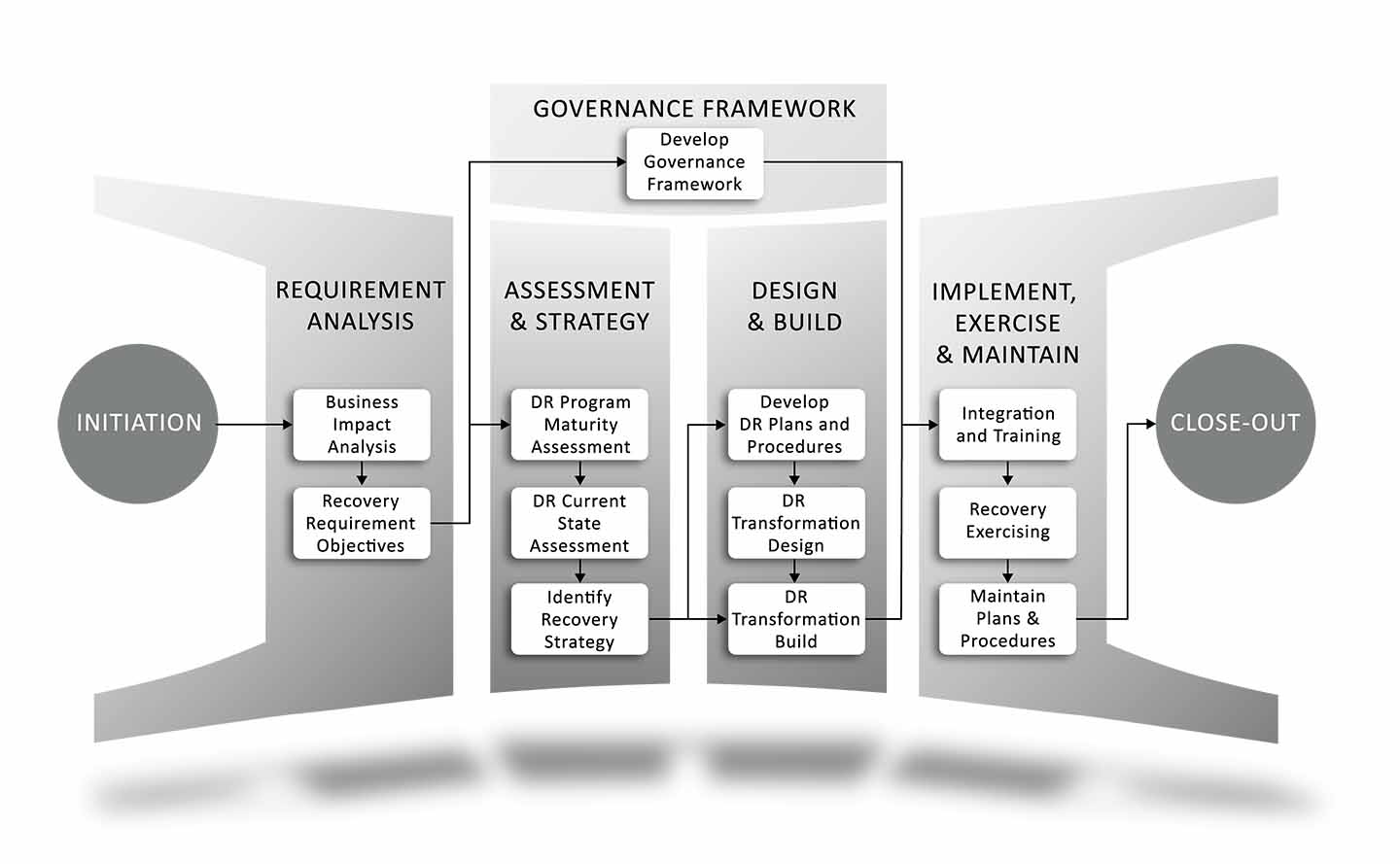
IT service continuity preparation: establish framework.
Whether your organization is looking to mature its ITSCM program or launch an inaugural program, it begins by establishing a framework so that a strategy and roadmap can be developed, implemented, and exercised toward maturity.
David-Kenneth Group’s ITSCM service is organized into five towers and designed to help organizations align their ITSCM plan with their day-to-day business operations. The five towers are:
- Governance Framework
- Requirement Analysis
- Assessment & Strategy
- Design & Build
- Implement, Exercise & Maintain
2. Requirements Analysis
Determining the requirements, i.e. Business Impact Analysis or BIA, helps an enterprise understand and prioritize the IT service continuity of mission critical business processes. The analysis provides the maximum amount of time acceptable for an outage for each business function relative to the risks and the financial impact. The results provide the ITSCM requirements that are used to prioritize critical business functions and supporting applications into ITSCM tiers and the ITSCM mechanisms.
3. Assessment and Strategy
A ITSCM assessment evaluates your current ITSCM capabilities using your current processes, procedures, and infrastructure deployment to identify any vulnerabilities that may impact recovery, fail-over, or fail-back to normal operations. Where gaps are identified, David-Kenneth Group recommends remediation processes and technical improvements to help meet the ITSCM requirements and mitigate vulnerabilities.
A strategy is created with actionable plans and technical procedures to “fill in the gaps” of the current ITSCM or to create a new one. The strategy is incorporated into the ITSCM program and include event identification, escalation, notification, continuity execution, and management of the event from event identification to a return to normal operations.
4. Design and Build
ITSCM design identifies and evaluates design alternatives that support the ITSCM strategy and are suitable for your environment and business goals.
David-Kenneth Group provides customized drawings, technical process specifications, deployment pattern design, and an implementation project plan as viable design alternatives. We also provide estimated capital expenses and operational cost estimates for budgeting and planning purposes
An ITSCM build offers assistance with modifying, building, and deploying the infrastructure and processes across the IT landscape.
5. Implement, Exercise, and Maintain
David-Kenneth Group implements the ITSCM program, provides training, and incorporates the ITSCM program into the Enterprise Services Continuity Management or Business Continuity Plan. We also develop a roadmap to manage change to infrastructure deployments and schedule awareness and exercise training.
When we perform exercises, via either tabletop or physical exercises, we document, observe, and recommend remediation action to improve the recovery and continuity posture. The results are delivered in a post-exercise summary report and can be incorporated into the IT Services Continuity Management or Business Continuity Plan.
David-Kenneth Group also establishes a maintenance schedule to review and update ITSCM posture and continuity procedures annually or after major change.
Executive leadership is crucial. Once the risk and potential impact of not having an effective IT DR plan are realized, senior leadership will make the required investments to protect the enterprise. Ultimately, the business case for a comprehensive plan is that it pays for itself when disaster strikes. The three critical success factors are
- having a plan,
- keeping the plan updated, and
- regularly exercising the plan.